Tor – The Onion Router By: David Rollé. What is Tor? Second generation Onion Routing Aims to improve on first generation issues Perfect Forward. - ppt download

Bergen Open Research Archive: Deanonymizing communications on The Onion Router (TOR) network with Deep Learning








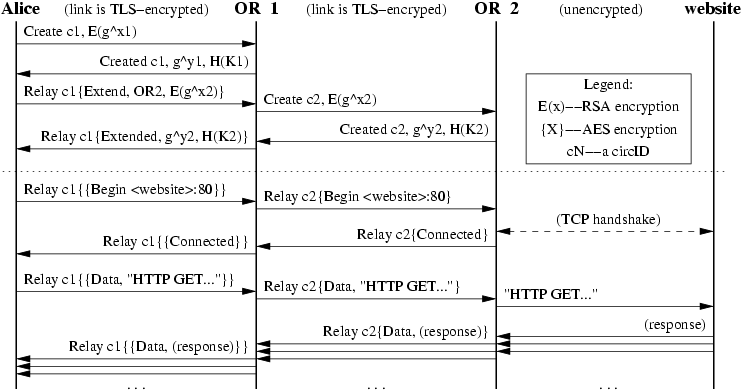
![PDF] Tor : The Second-Generation Onion Router ( 2012 DRAFT ) | Semantic Scholar PDF] Tor : The Second-Generation Onion Router ( 2012 DRAFT ) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3bd49342002397b7979ce3750d66782458026d09/7-Figure1-1.png)



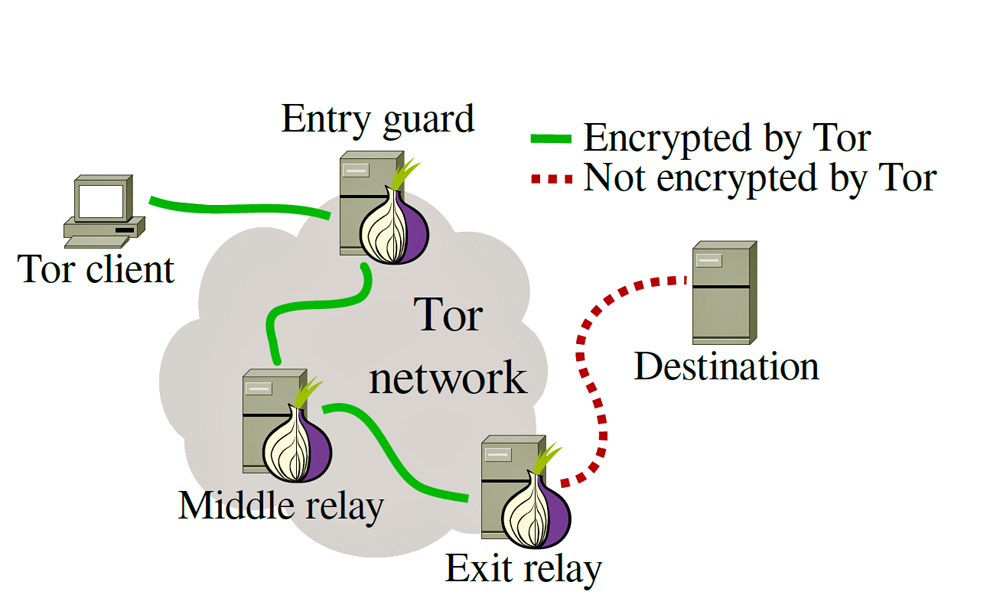
![PAPER REVIEW] Tor: The Second-Generation Onion Router – Kevin's Attic for Security Research PAPER REVIEW] Tor: The Second-Generation Onion Router – Kevin's Attic for Security Research](https://i0.wp.com/dandylife.net/blog/wp-content/uploads/2015/02/tor2.jpg?resize=654%2C361)